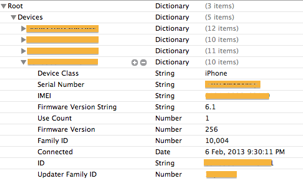
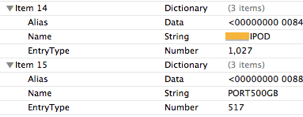
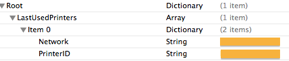
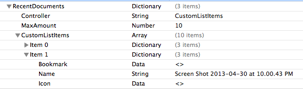
Prefetch files as defined in ForensicWiki is “Windows Prefetch files, introduced in Windows XP, are designed to speed up the application startup process.” Prefetch files contained metadata of forensic interests are:
- Executable file name (Unicode),
- Last Executed Timestamp,
- Executed Count, abd
- Volume ID.
Notable mentions to Prefetch forensic articles are:
- ForensicWiki & Windows Prefetch File Format
- DFINews: Decoding Prefetch Files For Forensics Purpose
- Windows Incident Reponse: Prefetch Analysis
Further to that, you will probably find many tools and articles on Prefetch file analysis. So I am just going to write only very briefly on it.
Prefetch files can be found at c:\Windows\Prefetch\ folder. For the purpose of this post, I will only focus on the file articles with the ‘pf’ extension.
Windows XP
- OS Version: Offset 00, length of 4 bytes (LE)
- 0x00000011: Windows XP
- File header: Offset 04, length of 4 bytes
- SCCA (0x53, 0x43, 0x43, 0x41)
- Unicode filename: Offset 16, length of 30 bytes
- Last executed time: Offset 128, length of 8 bytes (LE), Windows Filetime format
- Executed count: Offset 144, length of 4 bytes (LE)
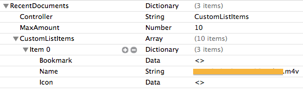
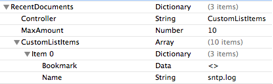
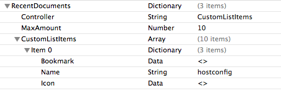
- VolumeID:
- Reference to Forensicwiki, Offset 108, length of 4 bytes points to the offset of section D of the prefetch file.
- Volume ID is located at Offset of section D + 16 bytes, for a length of 4 bytes
Windows Vista
- OS Version: Offset 00, Length of 4 bytes (LE)
- 00000017: Windows Vista
- File header: Offset 04, Length of 4 bytes
- SCCA (0x53, 0x43, 0x43, 0x41)
- Unicode filename: Offset 16, Length of 30 bytes
- Last executed time: Offset 128, Length of 8 bytes (LE), Windows Filetime format
- Executed count: Offset 152, length of 4 bytes (LE)
- VolumeID:
- Reference to Forensicwiki, Offset 108, length of 4 bytes points to the offset of section D of the prefetch file.
- Volume ID is located at Offset of section D + 16 bytes, for a length of 4 bytes
Windows 7
- OS Version: Offset 00, Length of 4 bytes (LE)
- 00000017: Windows 7
- File header: Offset 04, Length of 4 bytes
- SCCA (0x53, 0x43, 0x43, 0x41)
- Last executed time: Offset 128, Length of 8 bytes (LE), Windows Filetime format
- Executed count: Offset 152 length of 4 bytes (LE)
- VolumeID:
- Reference to Forensicwiki, Offset 108, length of 4 bytes points to the offset of section D of the prefetch file.
- Volume ID is located at Offset of section D + 16 bytes, for a length of 4 bytes
Windows 8
- OS Version: Offset 00, Length of 4 bytes (LE)
- 0000001A: Windows 8
- File header: Offset 04, Length of 4 bytes
- SCCA (0x53, 0x43, 0x43, 0x41)
- Last executed time: Offset 128, Length of 8 bytes (LE), Windows Filetime format
- According to my colleagues (JS and TB), Prefetch captured the last 8 executed time starting at offset 128. Each record is stored in Windows Filetime format.
- Executed count: Offset 208, length of 4 bytes (LE)
- VolumeID:
- Reference to Forensicwiki, Offset 108, length of 4 bytes points to the offset of section D of the prefetch file.
- Volume ID is located at Offset of section D + 16 bytes, for a length of 4 bytes.
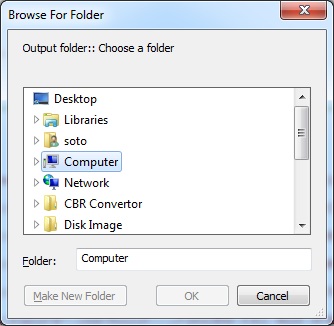
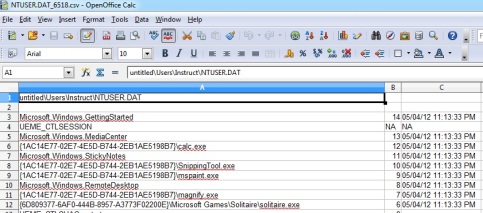
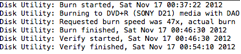
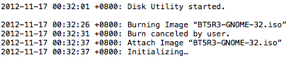
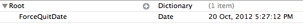
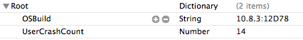
I wrote a simple EnScript to parse the Prefetch data and have tested it on limited numbers of prefetch files. This EnScript will parse Prefetch files with the file signature “SCCA”. The mode of operating the EnScript is illustrated in the following image:
Once the EnScript is run successfully, the output will save in the specified output file.
This EnScript is tested on limited number of Prefetch files. If you have any question or clarification or you find any bug, please contact me at davidkoepi – gm ail